E-mail Security Basics
E-mail Security (Phishing, Spam, etc.)
Email security contains many elements. It starts with the Division of Information Technology (DIT) filtering out known spam and fraudulent email. As always, you also play a part in good security – even email security. If you receive any e-mail that looks suspicious, or from anyone unknown to you, before responding to it or forwarding to any other recipient, please contact the DIT Service Desk at helpdesk@bowiestate.edu or 301-860-HELP (4357).
Let’s examine some of the basic aspects of fraudulent email.
Phishing
Phishing is the process of attempting to acquire sensitive information such as usernames, passwords and credit card details by masquerading as a trustworthy entity in an electronic communication. This is usually combined with a threat or request for information: for example, that an account will close, a balance is due, or information is missing from an account.
Phishing can also be used to install malware on your PC by way of clicking on a link in the message.
Spear Phishing
Spear Phishing adds a specific target to the above definition. Organized criminals research the target to discover work, commercial and personal relationships that can be used to customize the attack making it more effective. Hence, the word “spear” is used to further label this targeted attack.
Do NOT click links in e-mails. Type the address directly into a separate web browser address field. Make sure you recognize the web site address. Make it a habit to read your legitimate web site addresses.
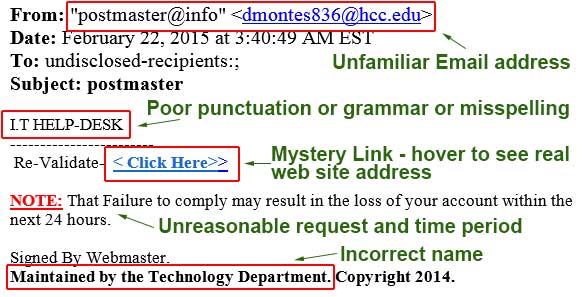
Suspect E-mail – Phishing Sample
Suspect email usually contains a number of oddities that reveal themselves with close attention. Examine any email sent from an unfamiliar source closely. If the email contains suspect elements such as poor English, a click here link, an unreasonable request or threat, and/or incorrect department names, be wary. It is best to contact the DIT Service Desk to confirm a suspect email rather than following the directions it contains.
About Web Site Addresses
As you access online information resources from the Internet, it is important to read the URL address of the displayed information (This information is displayed in the top of the web browser address field.)
Similar to your home address, the web address will tell you where the page is located. Consider the following example of what a legitimate web site address might look like (this one is fictitious):
![]()
- The blue (www) indicates this address is on the World Wide Web. (Similar to the Country in the physical address of your home.)
- The red (bowiestate.edu) indicates this website is a legitimate educational institution registered with EDUCAUSE. (Similar to the State in the physical address of your home.)
- The green (academics-research) indicates a folder or directory used to organize the web content and pages (Similar to the Street Name in the physical address of your home.) The brown (library) is another folder or directory within academics-research its used to further organize data.
- The black (index.html) indicates the exact location of the information displayed on this web page. (Similar to the Street Number in the physical address of your home.)
Passwords and E-mail
Your University username and password should only be used at bowiestate.edu web sites.
When the Division of Information Technology (DIT) upgrades computers, e-mail systems or the BSU network we NEVER send a link inside an e-mail which will go to a web site requesting that you login or enter your username and password. In fact you should NEVER reveal your secret password to ANYONE – it is and should remain your secret. If a login is necessary DIT will just tell you what site you need to go to with no link to click on. ALWAYS check the address – it must contain bowiestate.edu domain address.
Spam Email
If you receive spam messages, simply delete the email, or contact InfoSec@bowiestate.edu. Little can be done to prevent spam since the Internet is a public network. Filters can be used to remove most spam, but spammers are constantly working to improve methods in order to get their messages through. Some spam will get past the filters. DIT implements firewalls and other security measures to help fight against spam received at the University.
There are a few things you can do to help cut down on spam:
- Do not give your e-mail address without knowing how it will be used It may seem harmless to provide your e-mail address for a comment card for a restaurant or hotel, for example. However, companies often enter the addresses into a database so they can keep track of their customers. Sometimes these lists are sold or shared with other companies and could end up on a marketing list sold to spammers.
- Disable automatic downloading of graphics Many spammers send HTML mail with a linked graphic file that is used to track who opens the mail message. When your mail client downloads the graphic from their web server, they know you have opened the message. You can also disable HTML mail entirely and view your messages in plain text.
Do not unsubscribe
If the e-mail is from a disreputable or unknown source, do not click the "unsubscribe" or "remove" link in spam messages. Most importantly, do not respond, doing so confirms the validity of your e-mail address.
